What are phishing emails?
Phishing email messages are designed to steal money. Cybercriminals can do this by installing malicious software on your computer or stealing personal information off of your computer.
Cybercriminals also uses social engineering to convince you to install malicious software or hand over your personal information under false pretences. They might email you, call you on the phone, or convince you to download something off of a website.
For instance, a message like the one shown below, it looks a legitimate email, but on a closer look it is not.
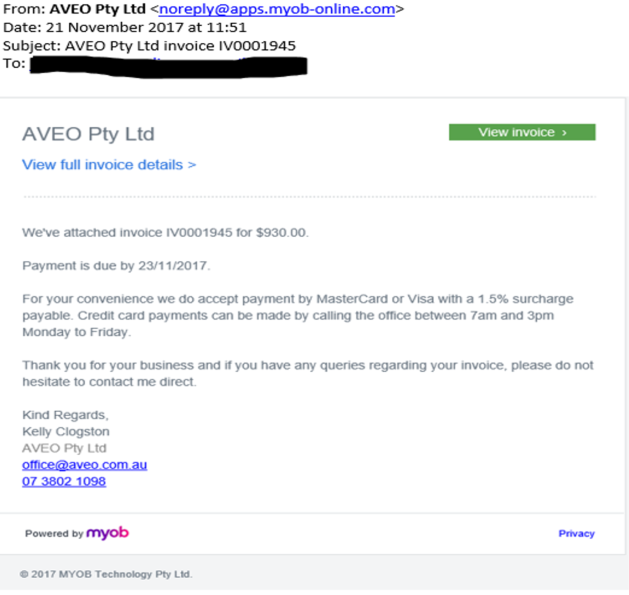
This email was received by Compliance Council this morning to one of our publicly available email addresses.
So how one can differentiate between a legitimate email and a phishing email?
Step 1: Spelling and bad grammar. Cybercriminals are not known for their grammar and spelling. Professional companies or organisations usually have a staff of copy editors that will not allow a mass email like this to go out to its users. If you notice mistakes in an email, it might be a scam. But in some cases, Cybercriminal can create an excellent email message like the one shown above.
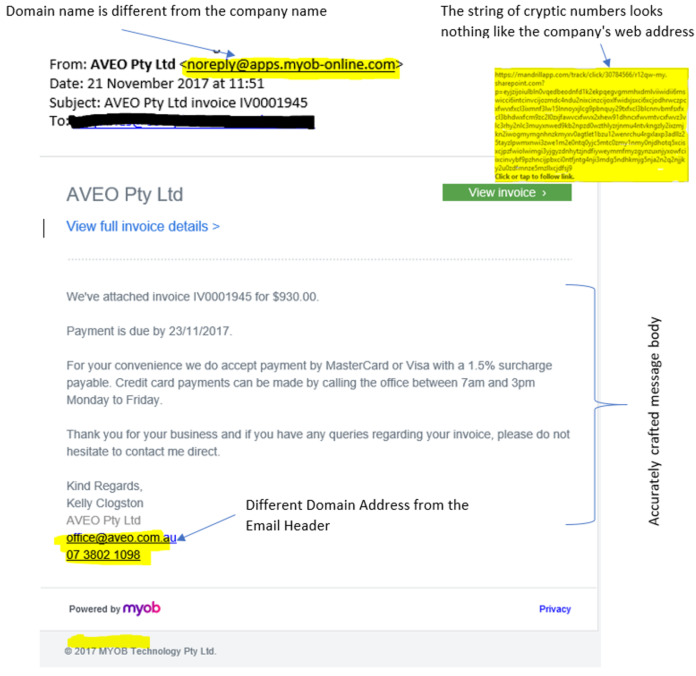
Step 2: Beware of links in email. If you see a link in a suspicious email message, don't click on it. Rest your mouse (but don't click) on the link to see if the address matches the link that was typed in the message. In the example below the link reveals the real web address, as shown in the box with the yellow background. The string of cryptic numbers looks nothing like the company's web address. You can verify the domain information through www.whois.com website.
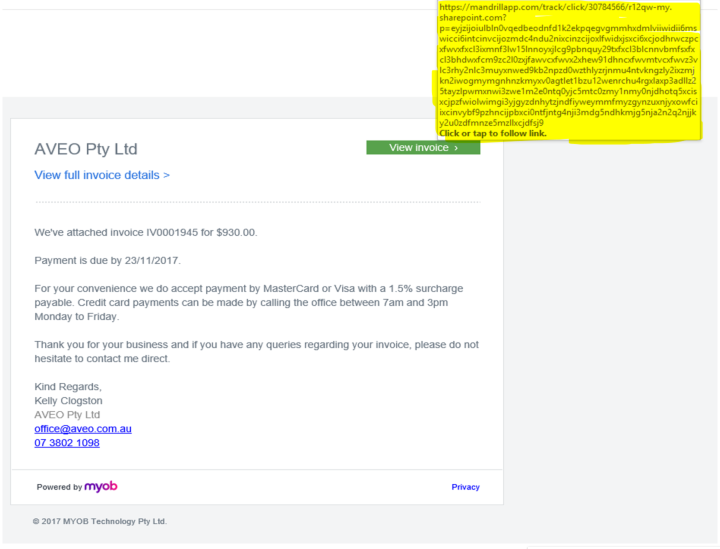
Step 3: Threats. Have you ever received a threat that your account would be closed if you didn't respond to an email message? Cybercriminals often use threats to play with human psychology.
Step 4: Spoofing popular websites or companies. Cybercriminal use graphics in email that appear to be connected to legitimate websites but take you to phoney scam sites or legitimate-looking pop-up windows.
What if you become a victim?
If you suspect that you've responded and/or click on the link, download the file, open the file and execute the contents, take these steps to minimise any damage and protect your identity:
- Report the incident to your IT department if it happens at your work place. If it affects your personal computer please contact the authorised dealer they will help you.
- Disconnect the equipment e.g. Laptop, tablet, desktop – PC etc from the internet.
- Execute the protection software and scan your laptop/pc/tablet for viruses, malware, trojans etc. In most of the cases protection software eliminates the viruses, malware.
- Change the passwords or PINs on all your accounts that you think might be compromised.
- Contact the bank or the online merchant directly, if you provide any account information. Do not follow the link in the fraudulent email message.
- Routinely review your bank and credit card statements monthly for unexplained charges or inquiries that you didn't initiate.
What if your business become a victim?
- If you're a small business owner, you need to be aware that you're a target for cybercriminals.
- Cybercriminals will often go to great lengths to convince you that their offer or request is legitimate, so it's important that you remain aware of typical scams and know what to do if you're targeted.
- You may subscribe to the ACCC's Small Business Information Network to receive all relevant ACCC small business news to your inbox.
- If you feel you have been a victim of a scam or targeted by cybercriminals, report it to Scamwatch.
- You can also follow @Scamwatch_gov on Twitter to keep up to date with the latest scams.
What can you do to better manage this threat?
- Subscribe to Stay Smart Online which is an government initiative to alert people to reported threats such as large scale phishing emails
- Implement an Information Security Management System that complies with ISO 27001 as it will require the organisation to implement various controls that will mitigate the risk of a phishing attack being successful in your organisation
- Raise awareness with your staff by distributing information and examples of phishing attempts in Australia so they understand how its not always obvious from looking at the email
Methods for raising information security awareness doesn't always have to be boring. Our favourite resources are the ones provided by Phisme. They have produced a series of posters based on popular TV shows such as House of Cards:



.jpg)
