The technology landscape is always evolving, and organisations that fail to keep up with these changes do so at their peril. Advances in technology offer numerous capabilities, but they also introduce new risks.
Business models today rely heavily on global digitisation, therefore broadening the attack surface and exposing gaps in security, in particular through the cloud. ‘The internet of things' is also posing serious challenges. We are now seeing companies offering IP enabled sensors in their products which can introduce multiple vulnerabilities. Many of the services today have an internet backing, and any connection to the web may cause a direct link to attackers.
Cyber security today is no longer just an IT issue. Many business activities such as market expansion, product launches, mergers and acquisition are now cyber connected. Today, we live and operate in an environment of digitally connected companies, people, and data which increases the risk of cyber attacks.
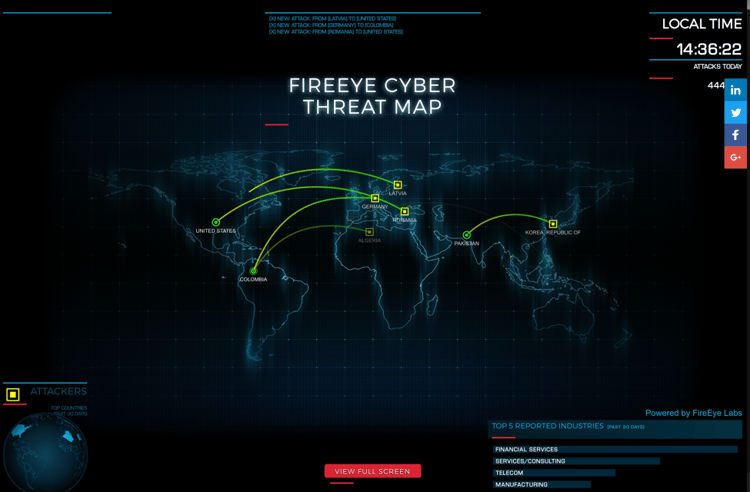
If you needed any more convincing on the prevalence of cyber security issues today, the FireEye Cyber Threat Map visualises the astounding volume of global attacks that occur each and every day.
The FireEye Cyber Threat Map
This is a real time map that charts malware detection. It includes malicious activity picked across email servers and transferred malicious software from particular websites. Cyber threats are visualised all over the world real-time. Attacks are scanned using intrusive detection, web antivirus functions and web and mail antivirus programs. From the data collected, you can get regular updates on countries and industries that are most at risk.
Changing Threat Motivation
Cybercrime is big business for the attackers, and they take it seriously as any other business. However, the threat actors have different motives. For example, the motive of ‘hacktivists’ is to damage the reputation of a company. On the other hand, cyber criminals seek to gain profit and run their operations similar to a legitimate business (though unethically). They can convert stolen data into cash, resulting in a loss in sales and of strategic partners, patent infringement and the release of counterfeit products.
A data breach often destroys a company's reputation and stakeholder confidence. It decreases market share, profit, return on capital and also jeopardises other investments.
What is Cyber Threat Intelligence?
Cyber threat intelligence is a process that enables a company to gather valuable information based on an examination of its unique threat predisposition. It can be tailored to the organisation's unique threat exposure and help to forecast breaches.
Threat intelligence encompasses technical information and provides specific indicators that are used to locate and mitigate current and potential threats. This information also presents the situational awareness of the threat landscape and helps organisations determine who might be interested in attacking them. However, for this information to be beneficial, it is important to develop a cyber-threat intelligence program that provides relevant and accurate reporting using tactical and strategic intelligence.
The loss of vital data, intellectual property, and strategic corporate communications can severely affect the long-term viability of an organisation. Understanding possible threats and vulnerabilities can help a company prioritise preventive and response strategies. Integrating a cyber-threat intelligence program can help you map out the threat landscape. This helps you take effective measures to prevent potential attacks.
How to Get Ahead of Cybercrime
Once a business realises it's facing an attack and begins to take action, cyber criminals respond by changing tactic and use a different approach. This makes it difficult for a company to manage an attack effectively. Threat actors are consistently inventing new tools to enable them to get information by identifying gaps and weak points in an organisation's security.
It’s difficult to know when a threat is looming, but by implementing the latest threat intelligence tools, you can anticipate and deflect possible attacks. Timely identification and reporting of breaches will impede the incentive of the attackers. Implementing a compliant information security management system makes you a more attractive business partner and increase confidence in your stakeholders and customers.
To learn more about the information security threats facing Australian businesses, download our free whitepaper below.



.jpg)
